What’s happening ‘inside’ encrypted Wifi networks?
Analyzing network connections with tools like Wireshark is usually straightforward if the traffic is accessible on a local interface. It’s a bit of a different story if the data cannot be captured on an endpoint, but must be tapped while in transit on a Wifi link between two devices.
In this case, I was interested in the communication between a Wifi-capable camera and the Android app provided by the camera manufacturer. The app can be used as a remote control for the camera and to download images on the mobile device. My particular interest was whether there is an extra layer of security (such as TLS) on top of the Wifi layer or the data is exchanged in plain representation.
Since Wifi is a shared medium and radio signals spread everywhere in the vicinity of the sender, eavesdropping on the raw bit stream is just a matter of an adequate antenna and tooling. Not surprisingly, every Wifi adapter in any computer covers the right frequency range, but it must be switched into a special mode — the monitor mode — in order to capture the entire traffic on a particular frequency band.
While drivers for Wifi adapters that support the monitor mode are mostly proprietary and expensive on the Windows platform, there is pretty extensive support for Linux, along with excellent tools such as iwconfig and airmon-ng. Mac users are in a particular comfortable position here, as macOS brings the right tools with easy-to-use frontends as built-in features of the operating system.
The tools for analyzing and capturing Wifi traffic are integrated in the ‘Wireless Diagnostics’ application that is launched using Spotlight (⌘ + Space):
Since Wifi networks use different frequencies (“channels“) that are usually picked randomly by the access point, the first step is to determine the channel used by the network of which the traffic shall be captured. The channel might change with every re-start of the device that is running the access point, so it is important to repeat this step with every capture attempt.
To see all Wifi signals that are visible from your device, open the ‘Scan’ window in the Wireless Diagnostics application:
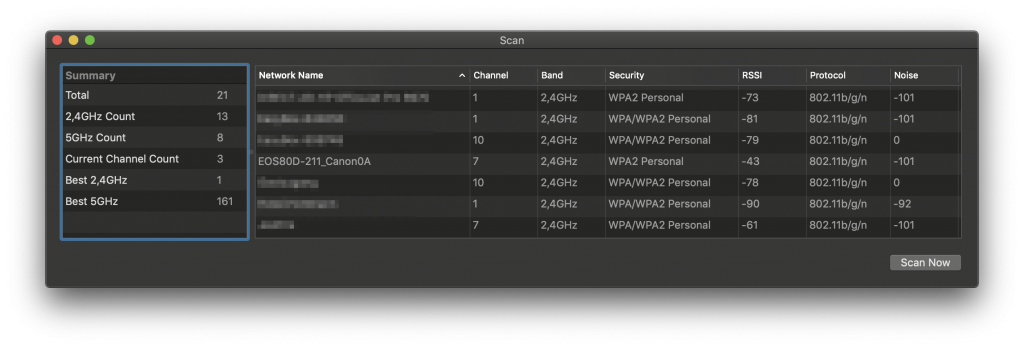
The window lists all Wifi networks that are visible to your computer. It shows that the network used by the camera is on channel 7. This is all the information needed to use the ‘Sniffer’ function, another window of the Wireless Diagnostics app:
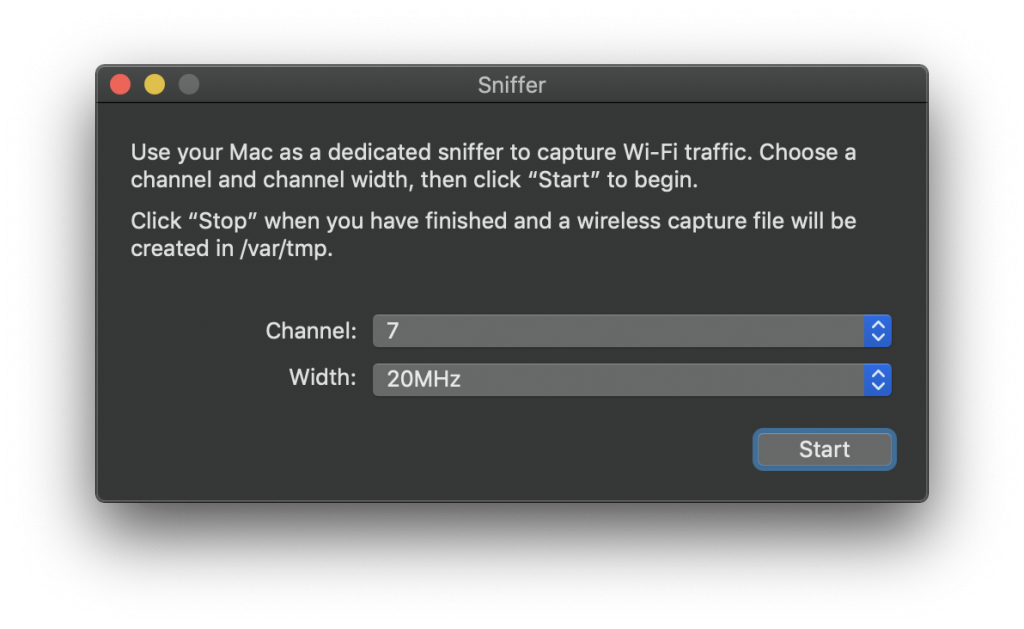
Pressing the ‘Start’ button captures the entire Wifi traffic on channel 7 that is within the range of your computer’s wireless network adapter. After stopping the capturing process, the tool offers to save the data to a file which in turn can be opened in Wireshark to inspect the recorded network frames.
Wireshark comes with a handy functionality that allows to decrypt traffic on the fly, that was captured from a WPA– or WEP-protected Wifi network (provided that you know the passphrase, of course). To be able to do this, it is essential that the recorded data sequence includes the beginning of the communication, where four so-called EAPoL messages are exchanged between the two devices. To ensure this, the mobile device may join the camera’s access point only after the capturing process has been started. After saving the recorded file, Wireshark’s filter function can be used to check whether the EAPoL frames are contained in the sequence:
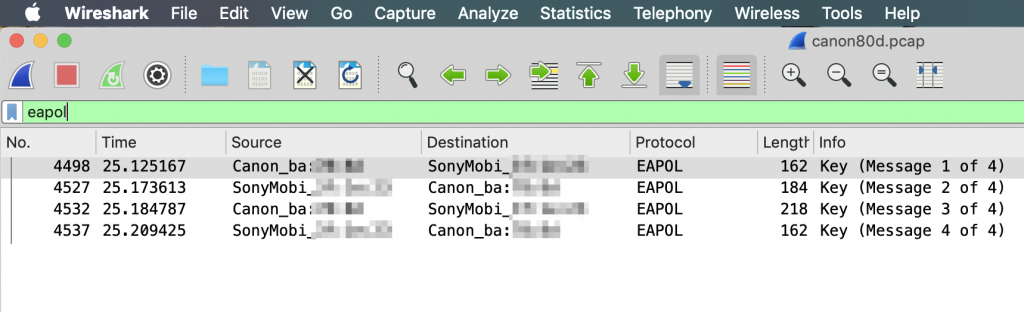
Now everything is set to inspect the communication between the camera and the app on the mobile phone. To see the traffic in plain text, the password of the camera’s Wifi access point needs to be provided. Wireshark requires the passphrase and the access point name to be entered as a single string with a colon mark (:) in between:
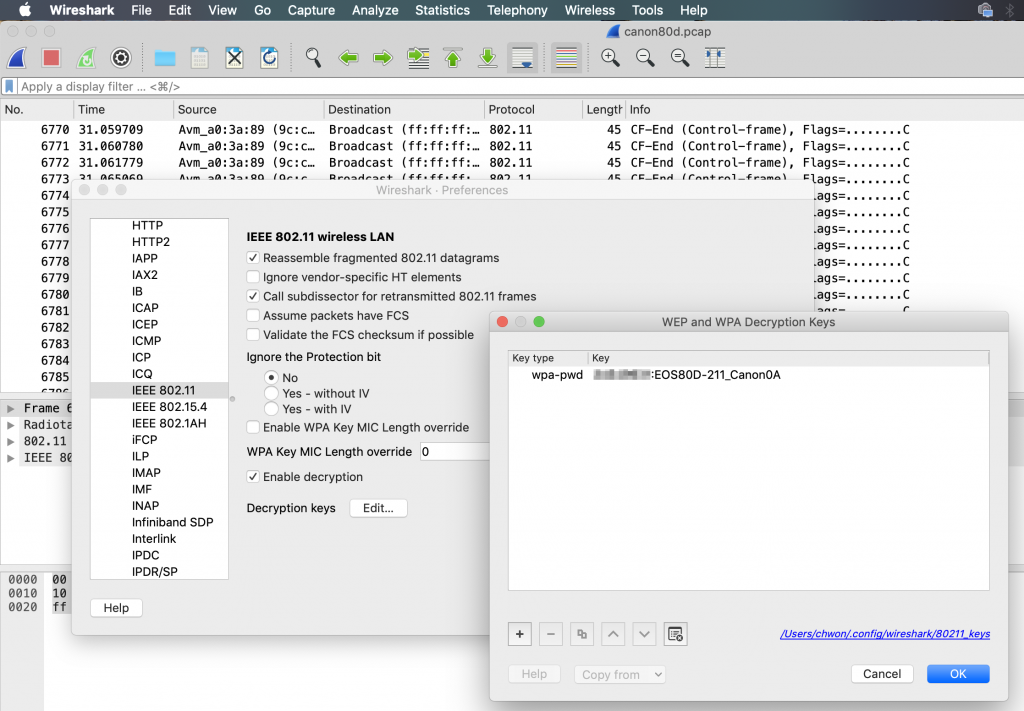
If everything fits together, you will usually see various TCP or UDP connections on top of an IP layer (a neat overview of the connections contained in the recorded trace is accessible via Wireshark’s ‘Conversations’ window).
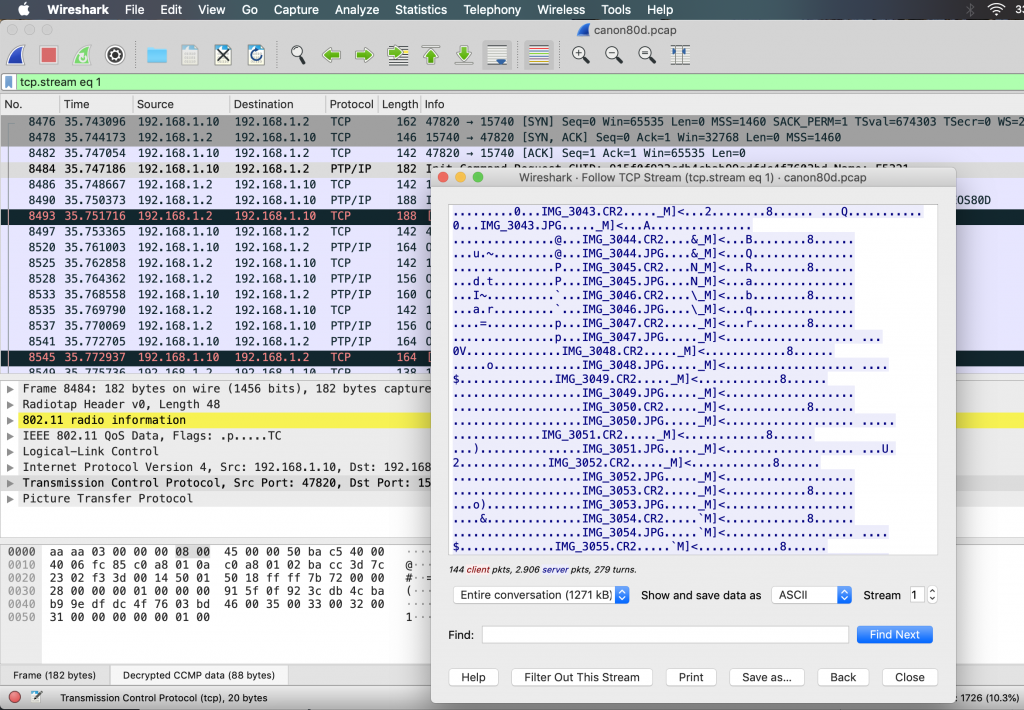
Coming back to the original question, it can be seen that there is indeed no extra layer of security besides the Wifi encryption. Wireshark correctly identifies the Picture Transfer Protocol over IP (PTP/IP) which is used by the camera to communicate with the Android app. Artefacts of the exchanged data can be easily seen in the TCP stream, such as the names of transfered image files: